Privacy and security are critical to the design, installation, and operational requirements of physical and cyber systems. Over the last ~15 years, security and cybersecurity have moved from being a begrudgingly funded expense line item to a key resiliency issue for the C-Suite and boards. The same story is evolving around privacy. Privacy has moved from being a legal and compliance issue that primarily arose in the case of a data breach or a finding by an auditor or regulator, to, again, something critical to people and organizations.
This focus is driven by the increase of laws around the globe and the increased frequency and reaction to both surveillance capitalism and grossly improper surveillance examples. Recent laws include the GDPR as well as many more recent privacy and surveillance laws in the United States, Canada, South America, Africa, and Asia/Pacific regions. The United States has a long and growing body of federal, state, and local privacy and surveillance legislation dating to the 1970s for information security and to the late 19th century initial legal consideration of the right to privacy. In addition to legal requirements there are global information technology frameworks and standards such ISO, NIST and others now include privacy.

Too often you find segmentation in organizations around privacy (lawyers) and security (IT and physical security). This hinders an understanding of the compatibility and interdependency of privacy and security.
Service providers must understand privacy from an operational perspective besides risk. Operational requirements enable the rights people have under the law. Embedding security and privacy in day to day operations will benefit all and should highlight and include the following:
- Privacy vs. Security is a false dichotomy.
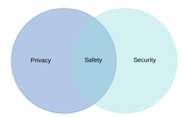
Privacy and secure complement and strengthen each other in many ways
2. Involving people always improves security and privacy, it also requires an investment in people and security and privacy services.
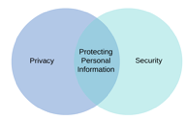
3. Security, Privacy and Usability must be embedded at the design stage.
4. You cannot have privacy without the appropriate level of security.
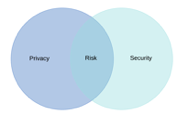
And you must understand how to perform the appropriate risk assessments for identity, surveillance, security and privacy risks across the business, operational, legal, technical and social goals of an organization and its ecosystem.
5. Transparency improves security and privacy.
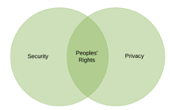
E.g., for any cryptographic system to be trusted, it is made public for peer reviewed and selected among a range of candidate approaches. There are many examples of how transparency creates and provides strength to security such a public revocation lists, public validation endpoints, even going back to 10 Most Wanted postings.
6. Reciprocity and proportionality are critically important requirements.
Reciprocity enables control and interaction with your privacy and personal information. As opposed to an “I Agree” button without the slightest understanding of what was in the print, or the cookies planted on your computer.
Proportionality is a balance of power at the point where a person might agree to something, usually with a legal entity, and other people. Asking people to agree to allowing their kids to use an application critical for them to attain schooling is not a fair/legal question.
7. Create a privacy point of contact, landing page and understand your public privacy profile.
Empower an individual to be the lead on privacy and work across that organization and business ecosystem. Create a privacy bug reporting system along with a privacy capability roadmap.
8. Creates a privacy code of practice.
This gap is often filled by industry associations that establish codes of ethics, conduct and practice.






